Cybercrime continues to rise. Recent DDoS-like network attacks exploiting the expansion and use of IoT (Mirai), or exploiting ransomware, demonstrate how any company can be the victim of an attack. Companies face branding, reputation or productivity damages, regardless of potential penalties and offsets to their customers. Companies have to define mitigation and recovery strategies to solve this problem. Create continuity plans have an impact on competitiveness, especially if these strategies are not efficient and adapted to their needs.
Communication and Internet service providers are key players in this scenario and have a clear opportunity to offer security solutions tailored to their customers.
The path towards virtualize networks
In order to take advantage of network capabilities and to improve efficiencies and response times in enterprise managed security services, network virtualization becomes an optimal security solution (vNSF or Virtualized Network Security Function). This is achieved by being able to deploy and modify the network as needed by software managers. An example of what type of solutions are being designed in the future in the network is the case of the SHIELD.
The SHIELD project
SHIELD is a project that is part of the EU’s Horizon 2020 program, with the aim of developing cybersecurity protection using network virtualization technologies and cognitive security techniques.
The idea is to use machine learning algorithms applied to network traffic to offer greater security to the services that are currently provided, mainly at the corporate context.
An extensible catalogue of vNSFs will allow you to monitor and mitigate attacks on the network, based on the decisions and recommendations of a cognitive system (DARE or Data Analysis and Remediation Engine) that will act through the network orchestrator for virtualized environments.
What does means Cognitive Security?
The cognitive capacity applied to the network relies on the use of Machine Learning. The foundation of this model is to develop and apply learning algorithms that are capable of extracting relevant information from the network about attacks and security incidents in an autonomous manner. Its main functions include identify attack patterns and generate recommendations in response. The learning algorithms are trained with real traffic, mainly in the final stages for testing and validation, and with synthetic traffic, in the initial stages, to be able to evaluate different algorithms. This approach is being analysed in both open source solutions such as the Apache Spot project, or in commercials such as CISCO Cognitive Threat Analytics.
How does SHIELD works?
In short, the project is using DARE, as a system of cognitive intelligence based on automatic learning applied to network traffic and security incidents. The project architecture includes the ability to collect and normalize information, as a preliminary step to use the algorithms. The difference with other existing solutions is the enforcement capacity.
The DARE results are delivered to the Network Operator to make the final decision based on the recommendations received. To be able to act on the network with a quick and concise response Service providers requires more powerful tools than the current network management solutions. This is where NFV (Network Function Virtualization) technology comes into play, using an NFV orchestrator (NFVO). The NFVO collects the recommendations and acts on the network by deploying the vNSFs, connecting and configuring them dynamically at network points where they are needed (for example, closest to the source of the attack) to protect customers and infrastructure. For this process, ETSI OSM (Open Source MANO) has been selected as an orchestrator, an open source solution, promoted by the standardization body of the ETSI NFV.
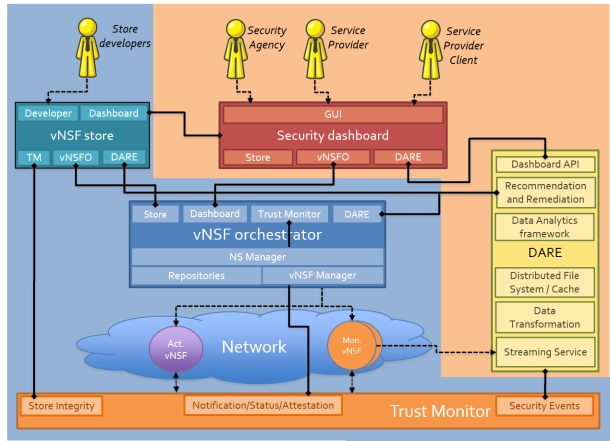
In addition, given the demanding security requirements expected for this solution, SHIELD is designing and implementing a Trust Monitor that attestate the integrity of the vNSF and its underline deployment on the network using hardware cryptoprocessors TPM (Trust Platform Module)
Finally, the great potential of this architecture is the diversity of security solutions that are expected to be offered. At present, IDS, Firewalls or antiDDoS vNSF are in process of integration
Results
To date the first results, outside the academic environment, have focused on the dissemination in the industry, such as the MPLS+SDN+NFV World Congress 2017 in Paris last March, where the project was announced.
Furthermore, SHIELD is already part of the ETSI NFV 001 v1.2.1 standard as a clear use case of Security as a Service or SecaaS (Security as a Service).
Next steps and trends
Beyond having a functional architecture, the first vNSFs, and the detection algorithms, it is expected in the course of this year 2017 to have a demonstrator for one of the situations that most impact today: detection and mitigation of DDoS (distributed denial of service) attacks.









