October 2013 marked an inflection point in terms of data leaks. That month, Adobe experienced a security breach in which more than 150 million user records were published on the web. Similarly, in December of the same year, personal information for more than 70 million clients of the North American company Target were leaked, motiving a mobilisation of cyber security resources valued at five million dollars. These incidents were the foundation for what we have experienced in 2015, and particularly in 2016.
According to a report recently published by ElevenPaths, the Telefónica cyber security unit, if during the first third of 2016 the rise in the leak of large databases was already significant, the systematic publication of incidents throughout the second quarter has been not only maintained, but has multiplied the number of credentials exposed over the Internet.
Types of Affected Platforms
Many sectors have been the subject of cyber security incidents linked to the leak of large databases. However, a very significant portion has been linked to the health sector, followed by the entertainment sector, social networks and government. In this sense, the report confirms that if one had to establish the characteristics of the average incident linked to the exfiltration of data in these months, said average incident would correspond to a cyber criminal incident linked to the health industry in the United States.
On the other hand, if we turn our attention to the most prolific perpetrators during this period, the reference is Peace or peace_of_mind. This cyber identity has become established in underground markets dedicated to buying and selling databases. But it’s not the only one. Other perpetrators have also risen to prominence, such as SonnySpooks, 0x2Taylor, Ghost Squad Hackers or bRpsd.
Nature of the leaked information
The most interesting information for cyber criminals is information that can be exploited immediately, which will mark, by the affected site’s profile, the nature of the user information that has been stored, as well as the security measures implemented by each platform.
In this sense, when the results are compared to those of the first third of 2016, we can see that a significant part of the leaked databases have exposed hashed passwords in their different formats. However, despite the fact that the relationship between the number of incidents in which clear text passwords were leaked and those incidents where the passwords were hashed is practically 2 to 1, the fact that the volume of hashed credentials is greatly superior to that of clear text passwords has been able to be confirmed. This is mainly due to the large volume of leaks coming from high profile domains such as Myspace, LinkedIn or Dropbox.
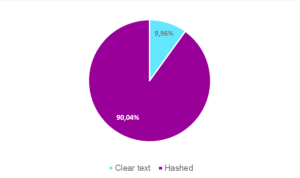
Figure 1. Comparison of leaked passwords that include clear text passwords in comparison to the number of credentials that include passwords in any form
Similarly, among the most repeated information identified are emails, passwords (both in plain text and hashed) and aliases and full names. However, there still remain numerous leaks in which we can also associate the profiles to postal addresses, IP addresses, and telephone numbers, providing an idea of the realization of the profiling that could be undertaken for each of the users.
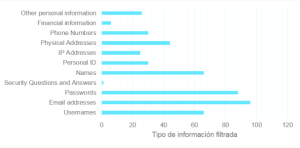
Figure 2: Number of analysed leaks in which each one of the different fields appears
Recommendations
The information obtained from these incidents can be used to perform other types of attacks, whether or not each service has reset its passwords. From the point of view of the attacker, having access to personal information is an element that can be exploited in different ways of extortion, in the manner already used in dating site platforms. Similarly, the information can also serve to configure directed attacks with higher probabilities of success using the details recovered from data leaks that expose personal information.
In order to minimise such risk, one should avoid reusing passwords and should change them regularly. In the same vein, using a password manager is recommended, as it takes on the responsibility of generating complex passwords while the user must only remember one single password. As well, it is preferable that platforms, if they so allow, use two-step authentication systems as an additional security measure to protect users from unauthorised connection attempts.









